Nikto Web Scanner is a Web server scanner that tests Web servers for dangerous files or common gateway interfaces, outdated server software and other problems. It performs generic and server type specific checks while capturing and printing any cookies received. Nikto also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated. The Nikto code itself is open source, but the data files it uses to run the programs are not. The code can also be found on GitHub.
Nikto is not designed as a stealthy tool. It will test a web server in the quickest time possible, and is obvious in log files or to an IPS/IDS.
Not every check is a security problem, though most are. There are some items that are “info only” type checks that look for things that may not have a security flaw, but the webmaster or security engineer may not know are present on the server. These items are usually marked appropriately in the information printed. There are also some checks for unknown items which have been seen scanned for in log files.
Features
Here are some of the major features of Nikto.
- SSL Support (Unix with OpenSSL or Windows with ActiveState’s Perl/NetSSL)
- Full HTTP proxy support
- Checks for outdated server components
- Save reports in plain text, XML, HTML, NBE or CSV
- LibWhisker‘s IDS encoding techniques
- Host authentication with Basic and NTLM
- Subdomain guessing
- Apache and cgiwrap username enumeration
- Mutation techniques to “fish” for content on web servers
- Scan tuning to include or exclude entire classes of vulnerability
checks - Guess credentials for authorization realms (including many default id/pw combos)
- Authorization guessing handles any directory, not just the root
directory - Enhanced false positive reduction via multiple methods: headers,
page content, and content hashing - Reports “unusual” headers seen
- Save full request/response for positive tests
- Maximum execution time per target
- Logging to Metasploit
To use, first boot up the Kali Linux and typing the command below:
nikto -h [address]
Nikto will return a lot of results, some of which are PHP version, XSS vulnerabilities, and server OS. If, at the end of the scan, Nikto finds vulnerabilities, it will return OSDVB codes. To check what the codes mean, you can visit www.osdvb.org.
Source: https://cirt.net/Nikto2; https://en.wikipedia.org/wiki/Nikto_Web_Scanner

 By entering the website you want to view, the Wayback Machine will display all dates in which it has kept track of the website. In the picture on the right, we look at www.kompas.com and we can see that the Wayback Machine keeps a very dense record of the history of the website (shown by the green circles on the dates). You can even choose on which year you want to visit, and the graph shows how much activity is tracked by the Wayback Machine in a year. The Wayback Machine will also give suggestions to your search, similar to Google suggestions.
By entering the website you want to view, the Wayback Machine will display all dates in which it has kept track of the website. In the picture on the right, we look at www.kompas.com and we can see that the Wayback Machine keeps a very dense record of the history of the website (shown by the green circles on the dates). You can even choose on which year you want to visit, and the graph shows how much activity is tracked by the Wayback Machine in a year. The Wayback Machine will also give suggestions to your search, similar to Google suggestions.


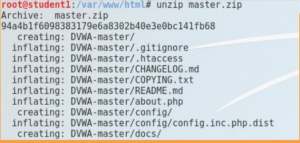

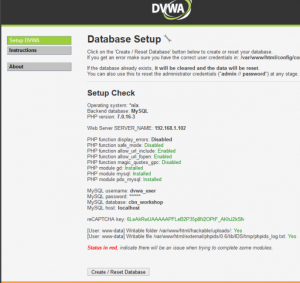
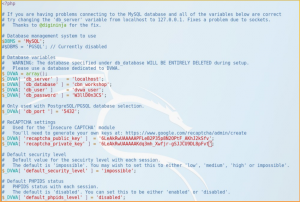 things that you should change is db_database, db_user, and db_password and don’t forget to fill in the recaptcha public key and private key. use site key for public and secret key for private.
things that you should change is db_database, db_user, and db_password and don’t forget to fill in the recaptcha public key and private key. use site key for public and secret key for private.